What you’ll learn:
- How automotive keyless entry is giving hackers a new way to steal cars.
- The three communication protocols involved in automotive keyless entry.
- How UWB works to make automotive keyless entry more secure.
With the COVID-19 pandemic shelter in place and significant numbers of employees now working from home, consumers are driving less and, unfortunately, seeing an increase in auto theft. In fact, with cars left unattended for longer periods of time, the Associated Press reported in May 2020 that major cities like New York City and Los Angeles have seen an increase in auto theft.
Even before this “new normal” we’re experiencing in the age of COVID-19, the National Insurance Crime Bureau (NICB) reported that 209 vehicles, on average, were stolen each day across the U.S. due to drivers forgetting key fobs in their vehicles, making for easy theft.
While leaving key fobs behind is an unfortunate mistake leaving drivers vulnerable to theft, another vulnerability is making car thefts easier—smart keys and smartphone car access.
While keyless entry is a standard on many cars sold today, the feature isn’t totally secure. For all of the convenience smart keys and smartphone access brings to drivers, it has given hackers a new way to unlock or steal cars through the wireless protocols that enable the entry. This is because current wireless protocols used for access are susceptible to criminals hijacking a car key’s signal.
Three communication protocols are involved in enabling a smart key or smartphone for unlocking a vehicle: Bluetooth Low Energy, ultra-wideband (UWB), and near-field communication (NFC), the latter mostly used as a backup. The three communication protocols, however, aren’t equal in terms of access security.
Bluetooth Low Energy
For quite some time, Bluetooth Low Eenergy (BLE) has been used in vehicles to unlock/lock the car and connect multimedia applications—to pair a smartphone with the multimedia console for voice calls or music streaming applications.
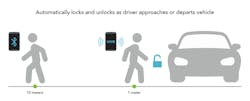
BLE is one of the communication technologies used for smart key or smartphone wireless access when approaching a car. In newer car keys, BLE communication is mainly used to track the approach of a driver beyond the 10-meter distance, while also preparing for UWB authentication. By using data packets, BLE relies on the measurement of signal strength to evaluate the distance of a driver.
Unfortunately, despite a certain degree of encryption, BLE can be subjected to jamming and relay or man-in-the-middle attacks. During a relay attack, the communication from the valid key is spoofed by a hacker by amplifying its signal strength and tricking the receiver into believing that the key is nearby. If a hacker can sniff and replay the data exchange between key and car, it’s possible to unlock the car and steal it.
UWB
Ultra-wideband, based on IEEE802.15.4z, is a newer technology standard that can be employed in wireless entry systems to prevent distance manipulation attacks—short UWB pulses are used for precise and secure time-of-flight (ToF) and angle-of-arrival (AoA) measurements. ToF measures the propagation time that it takes for the RF signal to travel between the transmitter and receiver. AoA measures the angle of an incoming signal using multiple antennas. Positions can be determined by having multiple angles, multiple distances, or a combination of the two.
With UWB, once the two devices (in this case, the smart key/smartphone and car) is within proximity, they begin ranging and calculating the distance with a centimeter level of precision between them. The smart key/smartphone can lock or unlock the vehicle when it’s within, for example, two meters of the vehicle, depending on the direction of movement (moving away or towards).
Unlike BLE, UWB is based on time, not signal strength. Therefore, a relay attack will not work on UWB, as the attack will add latency to the transmission and indicate that the key is actually far away from the receiver. In addition, adding a Scrambled Time Sequence (STS) into the UWB frame—an “encrypted” measure of a timestamp—prevents preamble insertion attacks and allows for even more accurate distance measurements. Figure 1 shows BLE and UWB distance for automotive access.
The new technical features enabled by UWB combined with a smartphone can enable not only safer access, but also new services such as locating your vehicle in a parking garage.
Redundancy with NFC
NFC provides the same locking and unlocking capability as UWB or BLE, but NFC is mainly used as a redundant system in the event the smart key’s or smartphone’s battery runs out. Redundancy in automotive applications is very important because a user doesn’t want to be in a position of not being able to unlock the car.
When an NFC passive device is brought within the near field of an active device (the car), the passive device “wakes” and communicates with the active device to perform an action, like unlocking the door.
While NFC is a much simpler communication protocol and therefore doesn’t have the same security benefits as UWB, it’s an excellent backup system for UWB because it’s very low power and requires much less battery from the device being used. In some cases, the smart key or smartphone may have a capability built in to recognize the level of power supply that’s available at a specific moment and select which communication protocol should be used to unlock the vehicle. It is, however, a less convenient solution than UWB because the car key needs to be held on an active part of the car.
Conclusion
All three technologies may be available in different smart keys and smartphones for enabling keyless vehicle entry. The comparison chart in Figure 2 summarizes the key technical aspects of each communication protocol.
While a UWB chip is more expensive than BLE, the wireless protocol provides significantly greater security in ensuring that only the driver obtains automotive access. Successful deployments of UWB-enabled smart keys or smartphones will depend on the accuracy of their fine ranging capabilities, making test compliance verification and performance validation imperative to successful implementation.
Joseph Sfeir is Director of Business Development at LitePoint.