This article is part of the Communication Series: The Cryptography Handbook
Members can download this article in PDF format.
In cryptography and within embedded security ICs, the physically unclonable function (PUF) is used to create keys that are generated on-demand and instantaneously erased once used. Because PUF depends on random physical factors (unpredictable and uncontrollable) that exist natively and/or are incidentally introduced during a manufacturing process, it’s virtually impossible to duplicate or clone.
PUF technology natively generates a digital fingerprint for its associated security IC. That can be utilized as a unique key/secret to support cryptographic algorithms and services, including encryption/decryption, authentication, and digital signature.
Except for the momentary duration of a cryptographic operation, the PUF key value never exists in digital form within the circuitry of the security IC. Further, since the key is derived and produced on-demand from physical characteristics of circuit elements, they’re never present in the device’s nonvolatile memory.
As will be described, any attempt to discover the PUF key through micro-probing or other invasive techniques will disrupt the sensitive circuitry used to construct the PUF key and render the output useless. Thus, they provide a level of security that’s very desirable in today’s embedded systems.
This short lesson is designed to outline and explain a simplified hypothetical PUF architecture and its usage. In reality, the PUF elements are much more complex and sophisticated. But this lesson should be enough to give the user a very good understanding of why PUF-based key generation can provide such excellent protection in cryptographic applications.
A Hypothetical Ring Oscillator-Based PUF
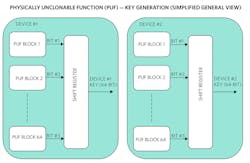
Figure 1 shows two separate example devices, each with a 64-bit PUF-based key (this is a simplified general view).
PUF—Key Generation
Each device in Figure 1 has 64 different PUF blocks that generate 1 bit of data. The bits are then shifted to create the 64-bit key. Now our target is to have independent keys for each of these devices that are repeatable over voltage, temperature, and age. Device 1 will produce a key with a sufficient number of bits that are different from the key produced by Device 2. Each of the device keys, though, will stay constant over the specified voltage and temperature range.
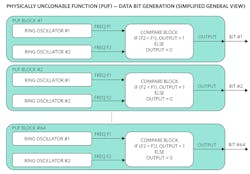
Data Bit Generation (Simplified General View)
In Figure 2, we show a simple PUF implementation scheme based on the frequency variation of ring oscillators. Later in this article, we will expand on ring oscillators and learn why they produce slightly different frequencies for each instance of the block.
For now, let’s assume that each PUF block has two ring oscillators that produce slightly different frequencies. In PUF block 1, F1 will be slightly different than F2. This will let the compare block produce a bit 0 or bit 1 based on whether or not F2 is faster than F1.
How does this design help with voltage, temperature, and age variations? We compare two values to generate the bits rather than basing it on one frequency output. Thus, if F2 increases with a higher voltage, F1 will also increase, but the delta between the two values should stay very much the same. This results in the same bit value produced with a different applied voltage. Similarly, the effects of temperature and aging can be mitigated.
As PUF block 2 to 64 are instantiated, the ring oscillator blocks inside them will produce slightly different frequencies from each other in an unpredictable way. This results in an unpredictable bit pattern for bits 1 to 64. Although the overall bit patterns can’t be predicated, the actual bit pattern produced is repeatable as each block always produces the same bit.
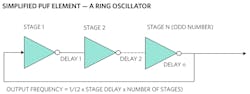
Simplified PUF Element—Ring Oscillator
A ring oscillator is constructed from an odd number of inverters arranged as shown in Figure 3. The output frequency of the oscillator hinges on the delay of each of the ring’s stages. From an integrated circuit perspective, this delay depends on wafer characteristics, including oxide thickness, capacitance, and threshold voltage of each transistor that makes up the inverter stages.
Due to imperfection and variation in the semiconductor manufacturing process, all of those parameters vary slightly and with complete randomness. No matter how controlled the process is, it’s impossible to avoid this random variation. All of this turns out to be a good thing for PUF implementation, because the key produced needs to have cryptographic-quality randomness.
A primary value that a PUF brings to cryptography is the inherent protection of the key/secret value that it derives and produces from the physical characteristics of circuit elements. As described in the ring oscillator example, electrically sensitive parameters such as threshold voltages, capacitance, and gate-oxide thickness directly influence delays through the circuit.
Probing or modifying the PUF, in an effort to obtain the key, in turn permanently modifies and disrupts these sensitive characteristics. This results in a change to the key value the PUF would output, making it useless and rendering the crypto IC permanently nonfunctional. Similarly, any attempt to reverse-engineer and clone a PUF results in a circuit that can’t output a key value, which is correct for the system environment in which the security IC is deployed.
ChipDNA PUF Technology
A new PUF technology developed by Maxim Integrated, known as ChipDNA, isn’t ring-oscillator-based like the hypothetical example. ChipDNA fundamentally operates from the naturally occurring random variation and mismatch of the analog characteristics of MOSFET semiconductor devices. This randomness originates from factors similar to those previously described: oxide variation, device-to-device mismatch in threshold voltage, interconnect impedances, and variation that exists within wafer manufacturing through imperfect or non-uniform deposition and etching steps.
ChipDNA also operates from a patented approach to ensure that the unique binary value generated by each PUF circuit has high cryptographic quality. In addition, according to Maxim, it’s guaranteed to be repeatable over temperature, voltage, and the device’s lifetime.
ChipDNA Applications
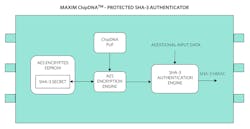
Figures 4 and 5 show use cases for ChipDNA PUF technology that’s integrated into a secure authenticator cryptographic IC.
Securing Stored Data
In this case, we’re using the ChipDNA PUF key, when needed, to decrypt the EEPROM-stored SHA3 secret used for an authentication sequence. Any attempt to obtain the secret from EEPROM will result in AES-encrypted data that’s useless to an attacker. In addition, any effort to probe the PUF will result in permanent disruption of its operation, resulting in the device being inoperable and again, useless to the attacker.
However, if the device isn’t tampered with, it will serve its purpose faithfully by generating the PUF key on-demand and decrypting the SHA-3 secret for a momentary authentication operation.
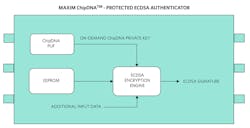
Key Generation for Authentication
In Figure 5, the ChipDNA PUF key is used directly as the private key for an Elliptic Curve Digital Signature Algorithm (ECDSA) signature computation. With ECDSA, by definition, the private key is a random number. ChipDNA is ideal in that it produces a high cryptographic quality random number. With asymmetric ECDSA there’s also a public key required to verify signatures, and it’s mathematically associated with the private key. Given the PUF key and, in this example, the ECDSA private key are never exposed outside the IC, the public key would be computed by the ECC engine within the part and stored in EEPROM for transmission to a host controller when requested.
This second example also demonstrates the use of ChipDNA PUF within the scope of benefitting key infrastructure and management. In more complex use cases, ChipDNA becomes the immutable root key of the security IC.
The next article in the series will cover the difference between hardware and software implementation of cryptographic solutions and some common applications.
Read more from the Communication Series: The Cryptography Handbook
Zia A. Sardar is Principal Member of Technical Staff at Maxim Integrated.