This video is part of TechXchange Talks and TechXchange: Cybersecurity
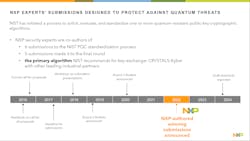
Securing data is very important these days, and public key encryption is one of the methods that's used all over the place. I spoke with Joppe Bos, Senior Principal Cryptographer at NXP, about a recent announcement by National Institute of Standards and Technology (NIST) and NXP regarding the next-generation CRYSTALS-Kyber algorithm. It's designed for the post-quantum world where quantum computers can break current encryption in minutes. This process has taken many years to complete, and it will take many more to get new systems up to spec (see figure).
Wong: So, Joppe, could you tell us why we need a new standard for public-key encryption?
Bos: Yeah, thanks. Publicly, encryption is one of the key components in cryptography, so I'll use symmetric key crypto hash functions and public-key crypto.
It was well-known already from decades ago that if one would have a quantum computer, one could use quantum algorithms to actually solve the hard mathematical problems. The Security Foundation of these currently widely used standardized public-key crypto algorithms.
For a long time, this was only a theoretical consideration. But now in the last decade, with the increase in knowledge and money and time spent on building quantum computers, the threat of these quantum computers with their quantum algorithms against our public-key standards became real, And so the U.S. government actually decided, just as they did for the other two areas, to create a call for participation and create a new public standard, moving away eventually from the two current standards in public-key RSA and ECC Elliptic crypto.
Wong: What does this new standard mean for the future of online security?
Bos: It will impact more or less all aspects of our day-to-day life. Everywhere we now use public crypto. The two main use cases for public-key crypto are of course key exchange and digital signatures.
Everywhere one of the two or both are used will be affected. It really ranges from sending messages with your favorite messenger app to just connecting to websites and your cyber connections to your bank. And to starting your car, because a digital signature in the secure-boot process is verified as well as getting secure updates on your phone.
So everything will be disinfected.
Wong: Now NXP is a co-author of one of the algorithms that NIST has selected for standardization to help protect against the threat of quantum computers. What is this algorithm and what does it do?
Bos: Yeah, yesterday NIST, the U.S. government, selected them after a lengthy process of more than six years. The winners of the standardization efforts in these two categories, the exchange and digital signatures.
And they announced which teams worked that finally got standardized, and one of the schemes where NXP is a co-submitter. A goal is the new worldwide standards for key exchange, which is called CRYSTALS-Kyber. This scheme would eventually replace, more or less, all the key exchange schemes which we're using nowadays. And the whole industry/financial industry, as well as all the cybersecurity connections if you browse the internet, will migrate to these new crypto standards.
Wong: What are the next steps now that NIST has announced its choice for standardization, how quickly will we need to update to this new standard?
Bos: Since this week, we know finally which new public-key post-quantum secure algorithms will get standardized. It will take roughly two years to turn this position into a standard. Once we have this new standard, of course, industry or probably some other sectors will already want to comply with these new standards.
Everybody is trying to take steps to actually comply with this. After two years when the standard is out, more and more people, of course, will ask and demand from large industrial players such as NXP, that they already are prepared and have their chips, their products to comply with the standards. Well, there will be, of course, a long transition period.
People need to build up trust where the first things will run hybrids. And there I mean, we run post-quantum crypto in combination with our classical cryptos. And then later we migrate to a solution which completely relies on post-quantum crypto. And we are already, because we are completely at the beginning of this chain where we design the secure elements and the platforms used in all sorts of products.
We already have been on top of this for multiple years to ensure that this whole transition period can happen very smoothly in practice.
Wong: Okay. So, what is NXP doing to help prepare for this new standard? Sounds like it's everything from chips to software.
Bos: Exactly. We are not only, of course, designing new hardware which ensures that we can actually run post-quantum crypto.
We're looking into ways how we can repurpose or reuse existing crypto accelerators designs for other tasks like RSA. We need to see that we can use it for post-quantum crypto. But, of course, we are also helping our customers with an impact assessment. What does it mean for their product? What does it mean in reality if you now need to migrate to post on some crypto?
Will the new keys, which for post-quantum crypto are significantly larger, even be fixed? If not, how can we resolve this? What is the impact on the performance requirements? We're helping there, but also we're helping with the whole crypto agility aspect. If you later want to upgrade in a seamless fashion, your products from the current crypto standards are easy to upgrade to post-quantum crypto ones.
How can you ensure that this is actually possible? These are all solutions and techniques. We help our customers with ensuring that they are prepared in the future for both quantum cryptos.
Check out more TechXchange Talk videos as well as the Cybersecurity TechXchange and our Cryptography Handbook.