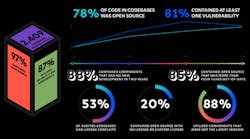
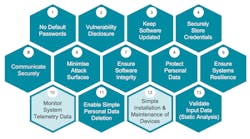
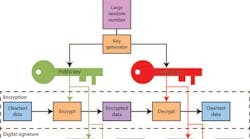
Cybersecurity
More content from Cybersecurity
More content from Cybersecurity
Security
Why Quantum Cybersecurity is Imperative
Oct. 30, 2023
Security
Cybersecurity from the Developer’s Seat
Oct. 26, 2023
Embedded
Air-Gapped Networks (Part 1): Air-Gapped Madness
April 11, 2023
Embedded
The Security and Storage Outlook for 2023
Feb. 15, 2023
Automotive
Automotive Safety and Security on the Road
Oct. 27, 2022
Embedded
Quantum Computing and Crypto Standards
Oct. 19, 2022
Embedded
Entropy for Embedded Devices
Oct. 13, 2022
Topics
TechXchange: VMs, Unikernels, and Containers
Sept. 12, 2022
IoT
Cybersecurity Suite Protects Edge AI Models
June 28, 2022
Embedded
The Cryptography Handbook
May 3, 2021
Automation
Pre-Boot Security Gets More Secure
March 12, 2021
Medical
Protecting Healthcare from Cyberattacks
Nov. 13, 2019
Embedded
Don’t Do It: Disabling SELinux
Dec. 19, 2018
Embedded
11 Myths About TLS
Nov. 8, 2018
Embedded
Secure Boot: What You Need to Know
Jan. 29, 2018
Automation
The Advantages of External Firewalls
June 13, 2017
Embedded
Crypto Essentials
Dec. 2, 2016
IoT
Ransomware, Backdoors, and Privacy
Feb. 22, 2016
Embedded
SELinux 101: What You Should Know
March 25, 2015